Blogs
Clustering and …
Clustering and Orchestration: Powering Modern Distributed Systems 🚀 Introduction In today’s rapidly evolving tech landscape, clustering and orchestration have become fundamental to managing complex, distributed systems. This post delves into these crucial concepts, exploring their …
Leaky Vessels
Leaky Vessels vulnerabilities Definition (What is Leaky Vessels?) Leaky Vessels is the name given to a set of vulnerabilities discovered and reported by Snyk on 2023 but publically-listed on January 31, 2024. This set of vulnerabilities allow an attacker to escape a containerized environment and is …
Containerization …
A Deep Dive into Containerization: Unveiling the Magic Behind Container Technologies In the world of modern software development and deployment, containerization has revolutionized the way we build, ship, and run applications. This article delves into the intricacies of containerization, explains …
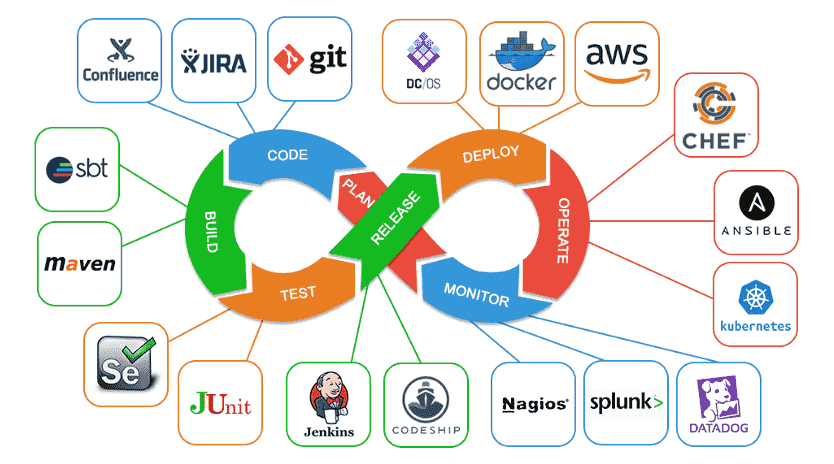
CI/CD in software …
The Crucial Role of CI/CD in Software Development In the ever-evolving world of software development, Continuous Integration and Continuous Deployment (CI/CD) has become an indispensable practice. CI/CD is not just a set of tools or processes; it’s a culture and philosophy that accelerates the …
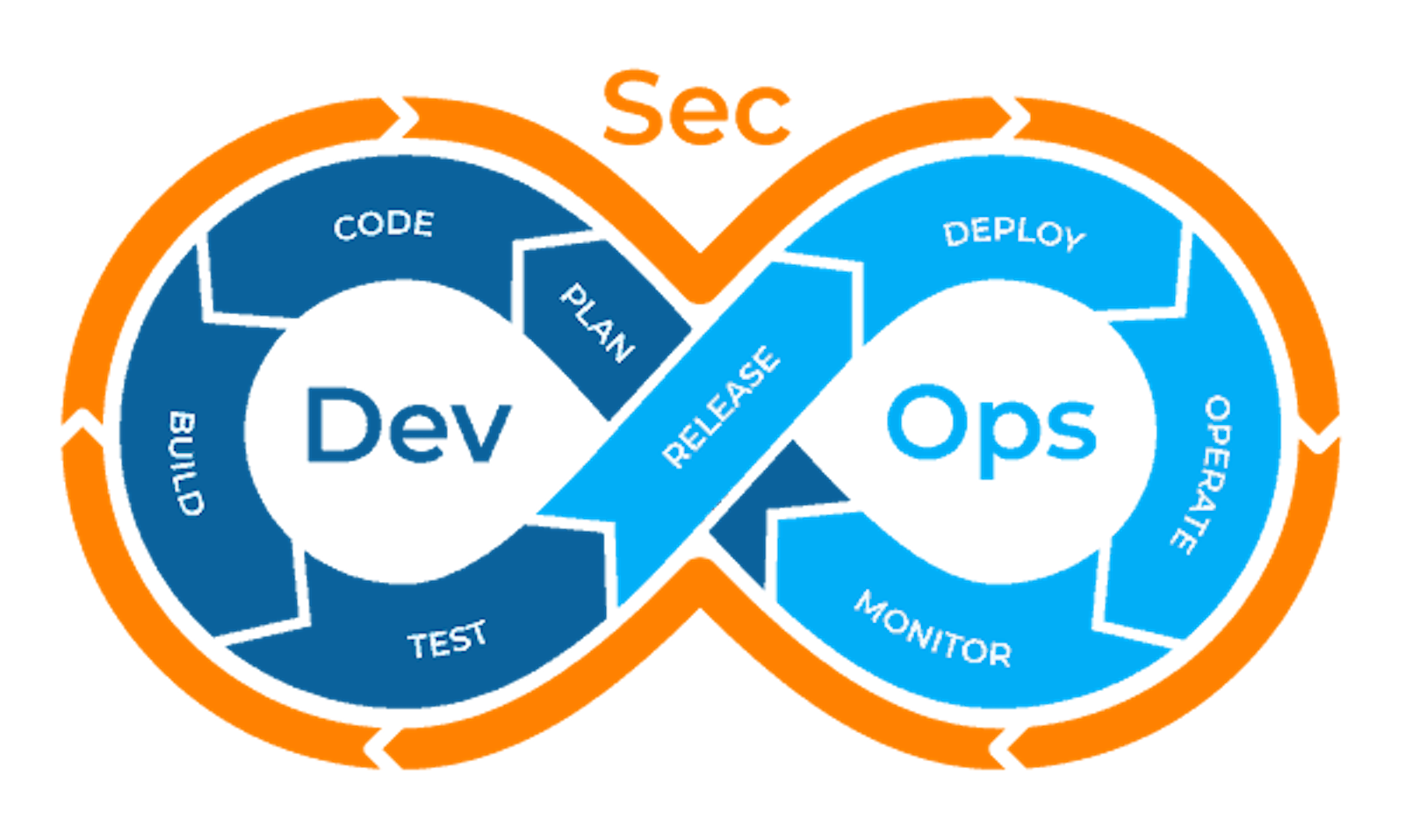
DevSecOps
Achieving DevSecOps Excellence: A Comprehensive Guide In the ever-evolving landscape of software development, the need for efficient and secure processes has never been more critical. Organizations strive to deliver high-quality software faster, and in pursuit of this goal, they often adopt DevOps …
Quantum Cybersecurity
CyberSec and Quantum Computing 1. Introduction In this guide, we’ll delve into the fascinating world of quantum computing, exploring its potential impact on our lives and the critical security concerns it raises. This article was written using ChatGPT since I’m not an expert in quantum …