Container security
Virtualization has been a game changer in IT for many years. By turning physical hardware into isolated virtual environments, technologies like virtual machines (VMs) and, more recently, containers allow us to run many workloads safely on the same machine. This separation means that if something goes wrong in one area, it’s much less likely to affect the rest of the system. As one study put it, “virtualization isolates the operating system and applications from the underlying hardware, reducing the risk that a breach in one instance will impact others” [Firesmith, 2017, IEEE]. Researchers such as Casalicchio and Iannucci (2018) have shown that when systems are kept up to date and strict access controls are applied, virtualization provides a robust foundation for security.
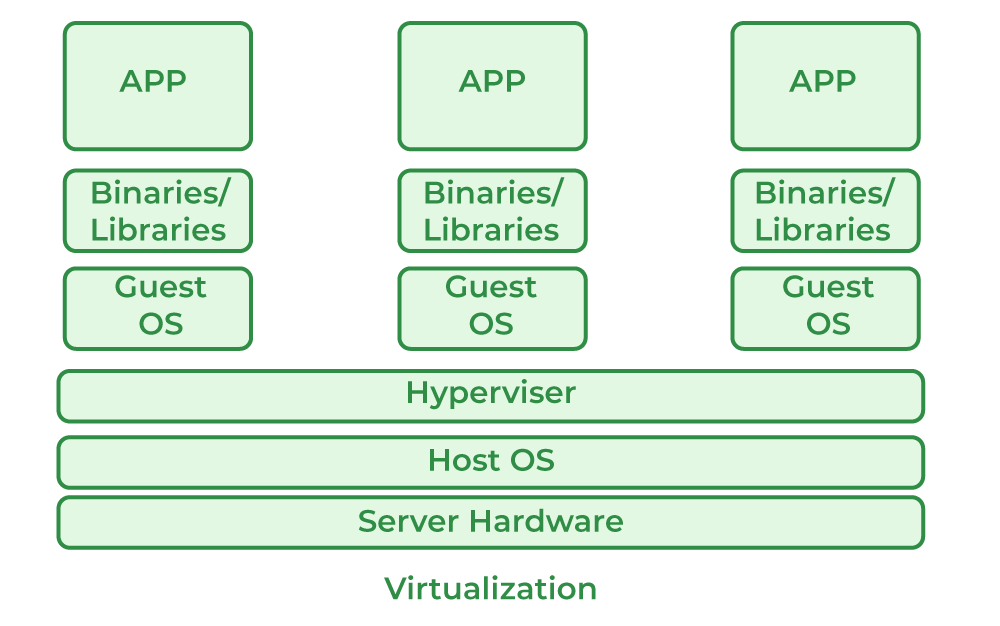 Figure 1: A simplified diagram of virtualization
Figure 1: A simplified diagram of virtualization
Container Security Fundamentals
Containers are like portable boxes that package an application with everything it needs to run smoothly. They ensure that apps behave consistently across different environments, but they also introduce unique security challenges. Let’s break these down:
Image Vulnerabilities: Research shows that container images, especially those used in data-analysis can harbor many vulnerabilities if not kept updated. Casalicchio and Iannucci (2018) explain that “frequent updates and minimizing extra packages are key to reducing the vulnerability footprint of container images”. Additional studies indicate that vulnerability scanning tools often miss key issues, highlighting the need for continuous monitoring.
Isolation Issues: Since containers share the host’s kernel, a vulnerability in the kernel might affect all containers. This shared model means that configuring namespaces and cgroups correctly is essential for maintaining isolation.
Privilege Escalation and Misconfigurations: Running containers with more privileges than necessary or misconfiguring them can provide attackers with opportunities to move laterally, so adopting a “least privilege” approach is critical
Below is a table summarizing these challenges and best practices:
| Challenge | Description | Best Practice |
|---|---|---|
| Image Vulnerabilities | Outdated or unnecessary packages increase risk | Regular updates; use minimal, trusted base images |
| Insufficient Isolation | Shared kernel may expose all containers | Use strong namespace isolation and container-specific OSes |
| Privilege Escalation | Excessive privileges may allow lateral attacks | Run as non-root; enforce least privilege |
Table 1: Key container security challenges and best practices.
Data Science in Container Security
Data science isn’t just about cool charts, it’s a powerful toolkit for boosting security by transforming raw log data into actionable insights. Let’s explore several key data analysis approaches:
Advanced Data Analysis Techniques for Container Security
Anomaly Detection: Algorithms such as Isolation Forests, Autoencoders, and One-Class SVMs help detect unusual behavior by flagging data points that deviate significantly from normal patterns. This is critical in identifying potential breaches before they escalate.
Predictive Analytics: Supervised machine learning models (e.g., Random Forests, Gradient Boosting Machines) analyze historical vulnerability data to predict future security incidents. Time series models, including LSTM networks, forecast trends and potential breaches based on past data.
Graph-Based Analytics: Graph theory is used to model relationships within containerized environments. By representing containers, processes, and network nodes as graphs, techniques like community detection, centrality measures, and shortest path analysis can help visualize and pinpoint vulnerabilities. For example, identifying which containers act as critical “hubs” in the network may reveal potential targets for attackers.
Clustering and Dimensionality Reduction: Methods like k-means clustering or PCA (Principal Component Analysis) help group containers with similar behavior or vulnerability profiles. This grouping makes it easier to manage and monitor security across similar sets of containers.
Natural Language Processing (NLP): NLP techniques can extract meaningful insights from textual logs, such as system alerts and error messages, by identifying key terms or sentiment changes that may signal a security incident.
Reinforcement Learning: Adaptive security systems can use reinforcement learning to optimize security policies in real time, learning from the environment’s feedback to adjust measures dynamically.
 Figure 2: A simplified data science workflow for anomaly detection
Figure 2: A simplified data science workflow for anomaly detection
Several recent studies underscore the role of these techniques. For example, Aktolga et al. (2023) provide a comprehensive survey of AI-driven container security approaches, while Oluyede et al. (2024) emphasize the importance of proactive vulnerability management in dynamic container environments.
Access Controls and Container Engine Management
Ensuring that only the right people and processes have access is essential for security. Container engines and orchestration platforms offer several key mechanisms:
User and Role-Based Access Control (RBAC): Platforms like Kubernetes allow you to define detailed roles and permissions. RBAC is fundamental for limiting access to container resources as stated in NIST SP 800-190. This means you can ensure that only authorized teams have access to specific functions.
Rootless Operation: Tools such as Podman enable containers to run without full root privileges by mapping the container’s root user to a non-privileged user on the host, reducing the risk of privilege escalation.
Security Modules and Image Signing: Using Linux security modules like SELinux, AppArmor, and seccomp helps enforce strict access controls. Docker Content Trust, based on The Update Framework (TUF) and Notary, ensures that only verified images are deployed. As Justin Cappos (2015) noted, “content trust frameworks add a vital layer of assurance by certifying the origin and integrity of container image" [https://medium.com/@maheshwar.ramkrushna/ensuring-docker-image-integrity-with-docker-content-trust-15aa312d66de].
API and Socket Controls: Securing APIs (e.g. Docker’s REST API) and critical sockets (like
/var/run/docker.sock) prevents unauthorized access to container management functionalities.
Below is a table summarizing these access control methods:
| Mechanism | How It Works | Benefit |
|---|---|---|
| RBAC | Define roles and permissions in orchestration platforms | Granular control over container operations |
| Rootless Operation | Run containers without full root privileges on the host | Reduces risk of privilege escalation |
| Security Modules | Use SELinux, AppArmor, seccomp to restrict container actions | Limits the actions an attacker can perform |
| Image Signing | Verify images via digital signatures (Docker Content Trust) | Ensures image integrity and authenticity |
Table 2: Access control methods in container engines.

Comparing Container Engines and Runtimes
The choice of container engine or runtime can have a significant impact on security. Here’s a friendly overview:
Docker Engine
Overview: A popular and user-friendly platform for building and running containers.
Security Highlights:
Comes with default security profiles (e.g., AppArmor/SELinux)
Supports image signing via Docker Content Trust.
Note: While popular, Docker’s daemon runs as root, so best practices are essential.
containerd
Overview: A lightweight engine commonly used with Kubernetes.
Security Highlights:
Efficient management of container lifecycles.
Works closely with runtimes like runc.
CRI-O and Podman
Overview: Designed for Kubernetes and security mostly.
Security Highlights:
- Reduced privilege risks and enhanced security through rootless approach to containerization.
gVisor and Quark
Overview: These runtimes add an extra security layer through sandboxing.
Security Highlights:
gVisor intercepts system calls in userspace for added isolation [https://gvisor.dev/docs/].
Quark employs a custom guest kernel and VM monitor for robust security [https://github.com/QuarkContainer/Quark/blob/main/README.md].
Below is a comparison table:
| Runtime | Key Features | Security Advantages |
|---|---|---|
| Docker Engine | Full-featured; popular; easy to use | Default security profiles; image signing |
| containerd | Lightweight; integrated in Kubernetes | Efficient lifecycle management |
| CRI-O / Podman | Kubernetes-focused; rootless (Podman) | Reduced privilege risks; strict RBAC support |
| gVisor / Quark | Sandbox-based; serverless-friendly | Extra isolation layer; custom guest kernel isolation |
Table 3: Comparison of popular container runtimes.
Academic Perspectives on Container Security
Researchers are deeply involved in exploring container security, and their findings offer practical insights. For example:
Oluyede et al. (2024) state that “the lightweight nature of containers, while excellent for speed, requires continuous and proactive vulnerability management” [https://www.mdpi.com/2673-4591/59/1/57].
Javed and Toor (2021) emphasize, “current vulnerability scanning tools miss a significant number of issues, calling for more research-driven approaches” [https://arxiv.org/abs/2101.03844].
Casalicchio and Iannucci (2018) remind us, “while performance and orchestration techniques have advanced, container security still poses open challenges that need further academic attention” [https://www.cse.msstate.edu/wp-content/uploads/2020/02/j5.pdf].
These academic perspectives reinforce the need for ongoing research and innovation, particularly by leveraging advanced data analysis to better understand and address vulnerabilities.
Containers vs. MicroVMs: A Friendly Security Comparison
Today’s world offers you the choice between using containers or a newer option called microVMs. Let’s break down the differences:
What Are Containers?
Containers are like lightweight, portable boxes that bundle an application with everything it needs. They’re fast to start and use fewer resources, making them perfect for scalable apps. However, because they share the host’s operating system, a flaw in the kernel could potentially affect all containers.
What Are MicroVMs?
MicroVMs combine the speed of containers with the robust isolation of traditional VMs. They run a minimal operating system on a lightweight hypervisor, adding an extra layer of security. This means that even if one microVM is compromised, it’s much harder for an attacker to move laterally [https://www.cse.msstate.edu/wp-content/uploads/2020/02/j5.pdf].
MicroVMs combine the best of both worlds: they offer the speed and resource efficiency of containers while adding an extra layer of security through stronger isolation—similar to traditional virtual machines (VMs). Here’s a closer look at what sets microVMs apart:
Enhanced Isolation: Unlike standard containers, microVMs run a minimal operating system for each instance on top of a lightweight hypervisor. This means each microVM has its own dedicated OS kernel, significantly reducing the risk that a single vulnerability could impact multiple instances.
Improved Security Frameworks: MicroVMs are built using modern frameworks that emphasize both performance and security. Two prominent examples are:
Firecracker: Developed by Amazon Web Services, Firecracker is designed specifically for creating and managing microVMs. It enables running thousands of microVMs on a single host with minimal overhead. Firecracker uses a custom lightweight virtual machine monitor (VMM) that ensures strong isolation between microVMs while keeping startup times extremely low—often in the order of milliseconds.
Kata Containers: An open-source project that merges lightweight virtualization with container simplicity, Kata Containers run containers inside lightweight VMs. This approach provides the security benefits of VMs—such as strong isolation and minimal risk of container escapes—while maintaining the speed and flexibility of containers.
Tool Integration: Both Firecracker and Kata Containers integrate well with popular orchestration platforms like Kubernetes. For instance, Kubernetes can now schedule workloads using microVM-based runtimes, allowing organizations to choose between traditional containers and microVMs based on their specific security and performance requirements.
Security and Performance Trade-offs: MicroVMs offer a slight performance overhead compared to standard containers because of the additional virtualization layer. However, this overhead is significantly lower than that of traditional VMs. The trade-off is worthwhile when extra isolation is necessary—especially in multi-tenant or high-security environments.
Below is a table summarizing the key differences between containers and microVMs:
| Aspect | Containers | MicroVMs |
|---|---|---|
| Isolation | Share the host’s OS kernel via namespaces and cgroups; efficient but riskier | Each microVM runs its own minimal OS on a lightweight hypervisor for stronger isolation |
| Attack Surface | Small footprint; however, shared kernel increases risk | Slightly larger footprint; dedicated OS reduces cross-instance attacks |
| Performance | Near-native performance with minimal overhead | Slight overhead compared to containers; still much faster than traditional VMs |
| Use Cases | Ideal for rapid scaling and microservices | Best for high-security or multi-tenant environments where isolation is critical |
Table 4: Overview of Containers vs. MicroVMs.
Data science techniques help by analyzing metrics such as startup times, resource usage, and security incident logs from both approaches, guiding organizations to choose the optimal balance between speed and protection.
| Feature | Kata Containers | Docker | GVisor | Podman |
|---|---|---|---|---|
| Type | Lightweight VMs | Native Containers | Application Kernel | Native Containers |
| Isolation | Strong (VM) | Weaker (Namespaces/Cgroups) | Strong (User-space Kernel) | Weaker (Namespaces/Cgroups) |
| Security | High | Lower | High | Lower |
| Performance | Moderate | High | Moderate | High |
| Overhead | Higher | Lower | Medium | Lower |
| Complexity | High | Low | Medium | Low |
| Daemon | Optional (can be integrated) | Required | N/A (Part of the Application) | Optional (Daemonless) |
| Use Cases | Security-sensitive workloads, Multi-tenant environments | General-purpose containerization, Microservices, Development | Security-critical applications, Untrusted code | General-purpose containerization, Development, Daemonless deployments |
Table 5: Summary of the key differences and trade-offs between different containerization technologies.
Advanced Data Analysis and Visualization Techniques
Data science can take security analysis even further by leveraging various visualization techniques and advanced analytics:
Interactive Dashboards: Tools like Tableau, Power BI, and Grafana help visualize security metrics in real time. These dashboards can display key performance indicators (KPIs) like anomaly frequency, resource utilization, and vulnerability trends.
Regression and Time Series Analysis: Statistical methods such as linear regression, ARIMA, and LSTM networks can forecast trends in security incidents. For instance, time series analysis can predict periods of increased vulnerability risk, allowing teams to preemptively apply patches.
Clustering and Dimensionality Reduction: Techniques like k-means clustering and Principal Component Analysis (PCA) help group containers with similar behavior or vulnerabilities. These clusters can reveal patterns that might otherwise be hidden in large datasets.
Graph Analytics: Modeling container interactions as graphs can provide insights into network behavior and dependencies. Using libraries like NetworkX and Neo4j, analysts can identify critical nodes and anomalous connections within the container network.
Research Notes and Further Reading
For readers interested in exploring container security further, here are some recent studies and academic publications that provide deep insights:
Container Security in Cloud Environments: A Comprehensive Analysis and Future Directions for DevSecOps (Oluyede et al., 2024, MDPI) – A detailed study on container security challenges and best practices. Read More
AI-Driven Container Security Approaches for 5G and Beyond: A Survey (Aktolga et al., 2023, arXiv) – This survey explains how machine learning techniques enhance container security in next-gen networks. Read More
Understanding the Quality of Container Security Vulnerability Detection Tools (Javed & Toor, 2021, arXiv) – An evaluation of container scanning tools that highlights the need for improved vulnerability detection. Read More
NIST Special Publication 800-190: Application Container Security Guide - A comprehensive guide from NIST with practical recommendations for securing containerized applications. Read More
The State-of-the-Art in Container Technologies: Application, Orchestration and Security (Casalicchio & Iannucci, 2018, ACM) – A thorough literature review covering performance, orchestration, and security challenges. Read More
Container Security: Issues, Challenges, and Road Ahead (ResearchGate, 2023) – A survey paper that explores emerging challenges and future directions in container security. Read More
Conclusion
In summary, container technology combined with data science offers exciting possibilities for enhancing application security. Virtualization—whether through traditional VMs, modern containers, or innovative microVMs—plays a vital role in isolating workloads and limiting damage if a breach occurs. While containers are fast and scalable, their shared nature means extra vigilance is needed, especially in access controls and continuous monitoring.
By leveraging a variety of data science techniques—from anomaly detection and predictive analytics to graph-based analysis and interactive dashboards, we gain valuable insights into our security environments. Ongoing academic research and a human, friendly approach to technology will help organizations find the perfect balance between performance and security, ensuring a safe and robust computing environment for everyone.
References
Casalicchio, E., & Iannucci, S. (2018). The State-of-the-Art in Container Technologies: Application, Orchestration and Security. ACM Digital Library. [Read more]
Firesmith, D. (2017). Virtualization via Containers. Carnegie Mellon University, SEI Insights. [Read more]
Javed, O., & Toor, S. (2021). Understanding the Quality of Container Security Vulnerability Detection Tools. arXiv:2101.03844. [Read more]
Oluyede, M. S., Mart, J., Olusola, A., & Olatuja, G. (2024). Container Security in Cloud Environments: A Comprehensive Analysis and Future Directions for DevSecOps. MDPI. [Read more]
Aktolga, I. T., Kuru, E. S., Sever, Y., & Angin, P. (2023). AI-Driven Container Security Approaches for 5G and Beyond: A Survey. arXiv:2302.13865. [Read more]
NIST Special Publication 800-190, Application Container Security Guide. (2017). National Institute of Standards and Technology. [Read more]
Additional reference: Container Security: Issues, Challenges, and Road Ahead (2023, ResearchGate). [Read more]

